7 Proven Methods to Address DevOps Challenges
In today's article, we'll go over 7 Proven Methods for Addressing DevOps Challenges.
Dev and Ops have cemented their place in the global software development community and are being adopted by an increasing number of organizations worldwide. DevOps effectively speeds up the resolution of certain types of problems and challenges that may arise during a project's lifecycle. DevOps as a Service in Singapore focuses on leveraging the best DevOps practices and tools to fast-track your cloud adoption.
Proven Approaches to Addressing Dev and Ops Challenges#
While Dev and Ops may introduce security flaws and compatibility issues among SDLC teams, there are ways to overcome these obstacles.
Consider implementing the following methods in your organization to strengthen DevOps security while maintaining a balance between different teams and DevOps as a Service for agility.

1. Implement Security-Oriented Policies#
Governance implementation and good communication are critical in creating comprehensive security settings. Develop a set of cybersecurity processes and regulations that are simple, easy to understand, and transparent in areas like access restrictions, software testing, gateways, and configuration management.
The notion of "Infrastructure as Code" (IaC) is central to DevOps. IaC eliminates environmental drifting in the workflow. Teams must maintain the parameters of each application area without IaC. IaC-integrated DevOps teams collaborate with a consistent set of security standards and tools to assist infrastructure and ensure safe, rapid, and scalable operations [(Tanzil et al., 2022)].
2. Adopt a DevSecOps Approach#
Encourage cross-functional partnerships across the DevOps lifecycle to ensure effective DevOps security. DevOps teams should collaborate and actively engage in the development lifecycle to achieve mutual security goals.
DevSecOps combines cybersecurity functions with governance to decrease the risk of security breaches caused by lax account restrictions and other flaws [(Nisha T. N. and Khandebharad, 2022)]. It goes beyond technical tools and software to ensure that security is a fundamental tenet of the company. DevSecOps encourages teams to understand and implement core security principles.
3. Use Automation to Increase Speed and Scalability#
Automation is critical for developing secure applications and environments. It mitigates the risks associated with manual mistakes and reduces vulnerabilities and downtime.
Effective automated technology and techniques are essential for security staff to keep pace with DevOps as a Service teams [(Jamal, 2022)]. Automated tools can be used for configuration management, vulnerability assessments, verification management, and code analysis.
4. Effectively Manage Vulnerabilities#
Incorporating security from the start of the SDLC helps in the early discovery of faults and vulnerabilities. Implement an effective vulnerability management system to track and prioritize the resolution of each vulnerability (remediation, acceptance, transfer, etc.).
Successful vulnerability management programs regularly adapt to comply with the latest risk reduction goals of the organization's cybersecurity rules and regulations.
5. Comply with the DevOps Lifecycle#
DevOps refers to the agile interaction between development and operations. It is a method followed by development teams and operational engineers throughout the product's lifecycle [(P P, 2019)].
Understanding the DevOps lifecycle phases is crucial to learning DevOps as a Service. The DevOps lifecycle is divided into seven stages:
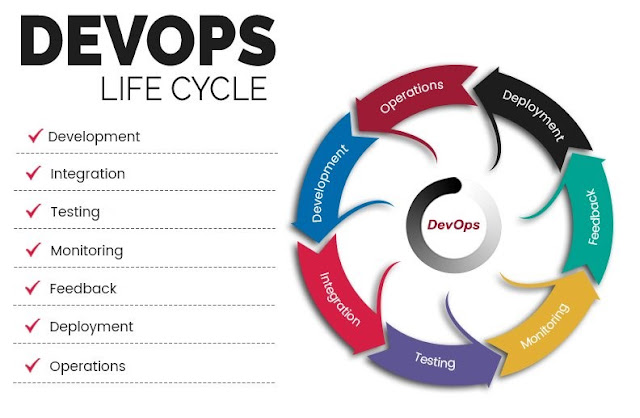
- Continuous Development
- Continuous Integration
- Continuous Testing
- Continuous Monitoring
- Continuous Feedback
- Continuous Deployment
- Continuous Operations
6. Implement Efficient DevOps Secrets Management#
Remove private data such as credentials from code, files, accounts, services, and other platforms for effective DevOps secrets management. When not in use, store passwords in a centralized password safe.
Privileged password management software ensures that scripts and programs request passwords from a centralized password safe. Develop APIs in the system to gain control over code, scripts, files, and embedded keys.
7. Implement Efficient Privileged Access Management#
Limiting privileged account access can greatly reduce the chances of abuse by internal and external attackers. Enforce a restrictive privileged model by limiting developers' and testers' access to specific development, production, and management systems.
Consider deploying advanced privileged access management systems, such as OpenIAM, to automate privileged access control, monitoring, and auditing across the development lifecycle [(Sairam, 2018)].
Conclusion#
The extended DevOps platform has propelled enterprises forward by delivering efficient solutions that aid in faster delivery, improve team communication, and foster an Agile environment.
While DevOps as a Service offers numerous benefits, it also presents challenges. Integrating security early in the DevOps lifecycle ensures that it is embedded at the core of the system and maintains its effectiveness throughout the product's lifespan. This approach protects the code against data breaches and cybersecurity threats.